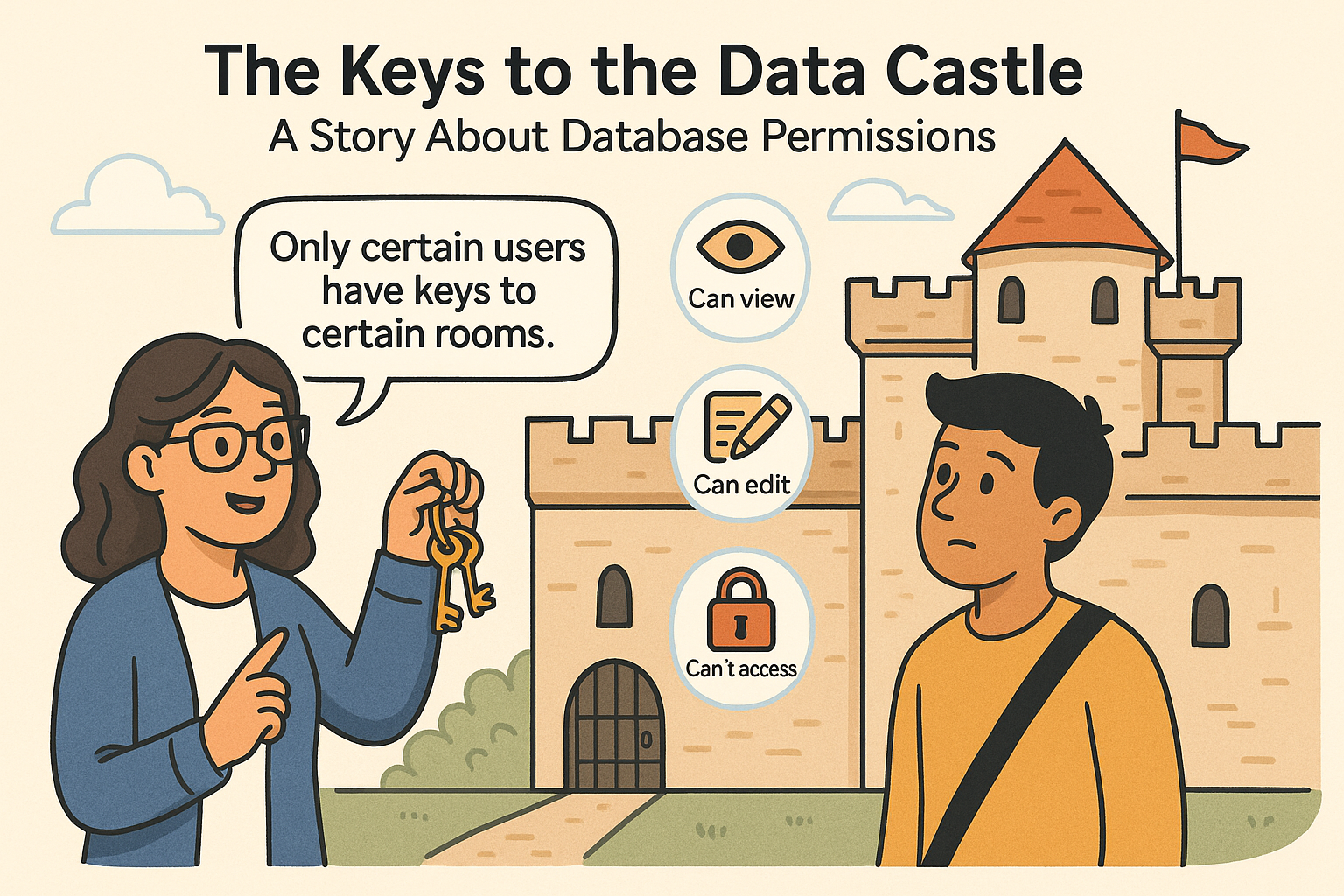
At a growing company named InfoNest, the HR team hired a new intern named Avi to help with data entry. On his first day, Avi asked:
“Can I see the salary table?”
The IT manager, Rina, replied with a smile:
“You don’t have the key to that room.”
Confused, Avi looked around. There were no rooms, no keys—just a computer.
Rina explained:
“Our database is like a digital castle, with many rooms. Some people have keys to enter any room. Others can only visit certain ones. That’s called permissions.”
Chapter 1: Understanding the Castle (Database)
The database stores all the company’s important information:
- Employee records
- Salaries
- Projects
- Logins
- Customer orders
Each part of the database is like a room, and each user is like a visitor with a set of keys:
- Some can read the data.
- Some can edit or delete it.
- Others can’t even see certain rooms.
| Role | What They Can Do |
| HR Intern | View and edit employee contact info only |
| HR Manager | View salaries, update roles |
| Finance | Access salary and tax records |
| Developer | Only see dummy test data |
| Admin | Full access to all tables and settings |
“This way,” Rina explained,
“everyone gets just enough access to do their job—but not more.”
Chapter 3: Real-Life Value of Permissions
- Protects Sensitive Data
Avi can’t accidentally email the CFO’s salary. Only HR managers can view it. - Prevents Mistakes
A marketing intern can’t delete 10,000 customer records by accident. - Supports Security & Compliance
When auditors review access, the company can prove who saw what—and when. - Enables Collaboration with Control
Multiple teams can work with the same database, but safely in their lanes.
Chapter 4: Temporary and Smart Access
When the IT team needed help from a contractor, they gave her:
- A temporary account
- View-only access to the “Projects” table
- Auto-expiration in 2 weeks
When she finished the job, the access was revoked automatically.
Avi asked:
“That’s like a guest pass at a museum!”
Rina replied:
“Exactly. Short-term, safe, and tracked.”
Conclusion: Right People, Right Access, Right Time
Database permissions aren’t about blocking people—it’s about protecting the data, the team, and the business.
Just like a castle:
- The cook doesn’t need the treasury key.
- Visitors need passes.
- Guards watch the gates.
And Rina? She’s the Keymaster—ensuring every user has the access they need, and nothing more.

Leave a Reply